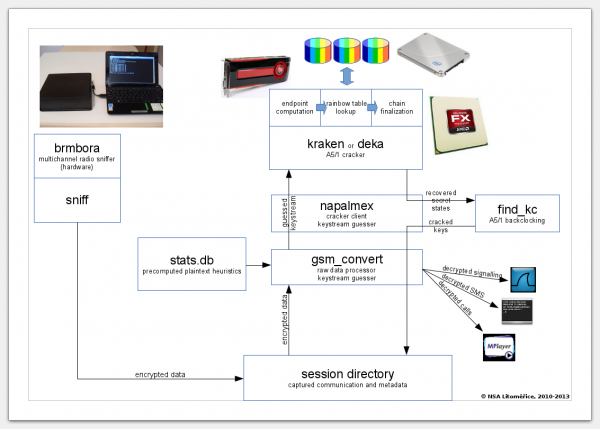
gsmtk - GSM sniffing toolkit
gsmtk contains handy tools to sniff GSM with osmocom-bb phones and recover encryption keys on sniffed data.
gsmtk is a fork of brmlab gsm toolkit. TL;DR brmlab GSM toolkit wants to support lots of great features, but it has serious bugs and no documentation at all.
gsmtk uses osmocom's ccch_scan as the sniffer. ccch_scan does not support the following two features, which are useful:
- Sniffing multiple communications in parallel using multiple phones (the master-slave architecture). One phone camps on CCCH and instructs other phones to follow assignments to separate channels. This is useful on crowded BTSes if you want to record all traffic.
- Recording traffic if the hopping sequence has been established after the ciphering mode command. This is useful for real-time call recording.
The first feature is supported in brmlab GSM toolkit, however, several frames are lost at the beginning of each communication. This may impair the ability to guess keystream in the encrypted part, e.g. because the System Information message is lost. This may be fixed by pre-synchronization of the slave phones to the BTS.
The second feature is implemented in brmlab GSM toolkit, but it stopped working and I don't know why (didn't invested more than a hour in debugging, though). It should be used with the sendfifo program.
Additionally, brmlab GSM toolkit does not work with hopping channels at all. This could be connected with the previous bug. This makes brmlab GSM toolkit completely unusable in some countries (Greece, Portugal) and losing about 10 % of traffic in some other countries (Czech Republic).
gsmtk does not have any automating scripts for sniffing with multiple phones. brmlab GSM toolkit has two of them - gsm_start_sniff.sh and gsm_spawn_master_slave.sh. I do not know how the first one should work and I have written the latter in 2012 and no documentation exists, so I cannot help you with it as I have no more information than you have.
I have written an A5/1 cracker that will help you to recover keys for data you have sniffed.
See also https://brmlab.cz/project/gsm/guesser
http://jenda.hrach.eu/gitweb/?p=gsmtk;a=summary
The README file should contain everything you need.